Check for upcoming public training Inquire about booking private training
Overview
Ever ripped open an IOT device and found yourself overwhelmed with how to make contact with the hardware you see inside? Ever put together an awesome hardware hack but need to clean it up, make it reliable, and make it repeatable?
This is a two-day crash course in rapid prototyping for hardware hacking. We’ll spend most of our time working hands-on to meet the mechanical, electrical, and protocol requirements for interfacing with our target hardware.
After a brief lectures on each topic, hands-on labs will guide attendees through:
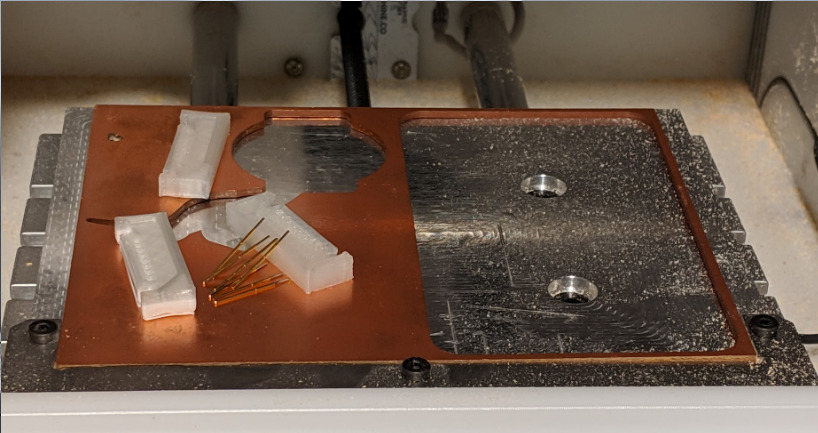
- Measuring, analyzing, and documenting a set of debug connectors
- Using CAD tools to design a custom jig to interface to the target
- 3-D printing, testing, refining, and using their jig
- Using CAD tools to design a small PCB interposer
- Milling, assembling, testing, and refining their PCB
- Characterizing electrical signals
- Designing simple circuits to protect both tools and targets
- Capturing unknown protocols
- Programming microcontrollers to ‘speak’ arbitrary protocols
- Putting all the pieces together into a polished hardware hack.
This course emphasizes how to connect to hardware for those that are already familiar with the what and why. It’s specifically geared towards attendees who have already completed an introductory hardware hacking course including some soldering experience.
Combining this course with Applied Physical Attacks 4: Hardware Implants would expand an additional opportunity to practice these skills.
Length
2 days
Audience:
Ripping open IOT devices to dump firmware and find debug testpoints is fun and effective, but everyone who tries this soon realizes that hastily soldering wires all over the place is unreliable. This course covers a series of techniques that enable you to quickly and reliably interface with all sorts of hardware devices, even when the manufacturer tries to make it difficult.
This course is specifically geared towards attendees who have some hardware hacking under their belt, but are interested in improving their ability to rig, retrofit, connect, and interpose wires into a system reliably and repeatably.
Format:
20% lecture
70% Lab
10% discussion
Outline:
This course is still in development. The specific hardware and software tools we will use are still being ironed out, but will fit into the overall outline:
- Part 1: Mechanical
- Lecture: Specifying, designing, and printing a debug interface jig
- Lab: 3D Printed Jig: Identify and measure testpoints, port into CAD tool, 3d print, and assemble, test, and refine a Pogo-pin jig
- Lecture: Specifying, designing, and milling an interposer PCB.
- Lab: PCB Interposer Design: Identify critical information from datasheets and measurement, design and capture an interposer schematic, layout a PCB, and mill the PCB.
Note: Ideally all manufacturing will happen day 1. If there are issues, some boards/prints will be manufactured overnight. In case of critical issues, some reference designs will be available to continue day 2.
- Part 2: Electrical
- Lecture: Techniques and conventions for making safe electrical connections to target systems
- Lab: Assembly and test - assemble pogo pins and wiring on jigs, solder components and headers on boards. Mechanically attach and test connectivity with multimeter and logic analyzer
- Part 3: Protocol
- Lecture: Techniques for custom I/O including bit banging, hardware assisted, DMA, and FPGA solutions
- Lab: Coding a microcontroller to speak a custom protocol,
- Part 4: Future Work
- Lecture: Making use of available tools, alternate techniques, and tradeoffs of different approaches
- Lab, if time permits: Interfacing with BYO target systems
Prerequisite
This two-day course assumes some experience:
- An introductory hardware hacking course (Joe Grand’s Hardware Hacking Basics, Applied Physical Attacks 1: Embedded and IoT Systems) or similar knowledge
- Soldering experience is beneficial - we’ll be able to help, but won’t have time to teach how to solder
- Practice poking around a few hardware devices on your own