Hardware Security Resources, LLC offers courses, workshops, and curriculum to help introduce and ramp existing software security experts and hardware validation experts into the field of hardware security.
Applied Physical Attacks... Online!
For the second year in a row, Black Hat surprised me by getting training registration up earlier than expected - Kudos to them! That means they already let t...

The Big Hack - What did we learn?
Happy “The Big Hack”-iversary! What have we learned in a year?

The Big Hack - Disconnecting the Dots
Happy “The Big Hack”-iversary.
Applied Physical Attacks CanSecWest 2018
The initial offering of Applied Physical Attacks classes covering Rapid Prototyping and Hardware Implant techniques at CanSecWest was a success! A room full ...

Applied Physical Attacks on Embedded and IOT Systems AND Hardware Pentesting, Back-to-Back
The upcoming edition of HardwareSecurity.training will take place in Redwood City, CA. We’ve got 9 choices of hardware-focused training over the course of 4 ...

Applied Physical Attacks on Embedded and IOT Systems at Kiwicon
This 2-day class will be offered at Kiwicon in Wellington, NZ. One great aspect of Kiwicon is that in addition to paid seats, there are also free seats which...

Applied Physical Attacks on Embedded Systems at Black Hat Chicago Trainings
This 2-day class will be offered in Chicago at Black Hat’s standalone training event. Registration is still open.

Do I Have a Hardware Implant?
I’ve gotten lots of inquiries from people who want to know if I could analyze some hardware for them or could recommend someone who might. I’ll be blunt - mo...

Hardware Implants
There’s recent news about some really interesting hardware implants. I wanted to take a bit to share more technical thoughts and details that can’t be reduce...

Applied Physical Attacks and more at Black Hat USA
This summer, The Embedded Systems and Hardware Pentesting classes will return to Black Hat after selling out last year. In addition, as a collaboration with ...

Congratulations, your submission has been declined!
Congratulations, your talk has been declined! Many of us have been disappointed or relieved by a rejection in the past few days. As a follow-on to my previou...

Embedded Systems at InfoSec in the City, Singapore
Infosec in the City’s inaugural event happened in may, and before the conference was the first public offering of Applied Physical Attacks on Embedded System...

Embedded Systems & Hardware Pentesting at HardwareSecurity.Training in Rockville, MD
We managed to repeat our HardwareSecurity.Training success on the east coast this spring. We’re continuing to learn what works best for our style of event. T...

Submitting To A Cfp
I recently posted a twitter thread with some advice for submitting to CFPs and writing abstracts. I’m FINALLY containing it in a blog post with a few correct...

Embedded Systems & Hardware Pentesting at SecurityTraining.Berlin
The first international HardwareSecurity.Training was a success!

Applied Physical Attacks and Hardware Pentesting at CanSecWest 2018
This was the first offering of the advanced Hardware Pentesting class at CanSecWest. It’s geared towards people who’ve already dabbled with a little bit of h...

Formally announcing 'Hardware Attacks, Threats, Risks, and Mitigations'
For the second year in a row, Black Hat surprised me by getting training registration up earlier than expected - Kudos to them! That means they already let t...
New For 2018
In between the busyness of last fall, I had some insight into what 2018 would look like and how I and SecuringHardware.com could rise up to meet it. I’ve spe...

2017 Wrapup
This year marks the end of SecuringHardware.com’s 5th successful year in business. Looking back, however, the definition of ‘success’ has improved significan...

Embedded Systems & Hardware Pentesting at HardwareSecurity.Training in San Francisco
The inaugural HardwareSecurity.Training event in San Francisco was a success!

Physical Attacks on x86 Systems at HardWear.io in The Hague
Once again, I taught Applied Physical Attacks on x86 systems at HardWear.io in The Hague, marking 2 years since the first time it was offered at the inaugura...
Embedded Systems at 44CON in London
44Con 2016 was the first time I taught Applied Physical Attacks on Embedded Systems. In 2017, instead of a small room and a handful of people, we sold out to...

Applied Physical Attacks on Embedded Systems and Hardware Pentesting at Black Hat USA
The first Back-to-Back run of these two classes was a great learning experience for both me and the attendees. Most things went well even though a few things...

HardwareSecurity.Training coming in November
There’s a short list of professional hardware security trainers in the world, and most of us have teamed up to deliver a set of hardware security trainings s...

First Crack at Applied Physical Attacks and Hardware Pentesting
The first run of this class was a success! A full class gathered at Widmer Brewery in Portland and hacked around on a custom IOT target system as well as an ...

Applied Physical Attacks on Embedded Systems at TROOPERS17
This class sold out which gave us the opportunity to test the limits of how much gear we could get to and from an international class intact. We were also si...

Applied Physical Attacks on x86 Systems and Embedded Systems at CanSecWest 2017
CanSecWest will be held in Vancouver, BC, Canada on 15-17th of March. Dojos will be held before the conference on 11-12 and 13-14 March 2017

Formally announcing 'Applied Physical Attacks and Hardware Pentesting'
Black Hat already let the cat out of the bag when they opened registration earlier than I expected, but I’d like to take a moment to share the background and...

Taking January Off
After wrapping up a successful 2016, I had a unique opportunity to take January ‘off’. This doesn’t mean it was a vacation, but that I finally had the opport...
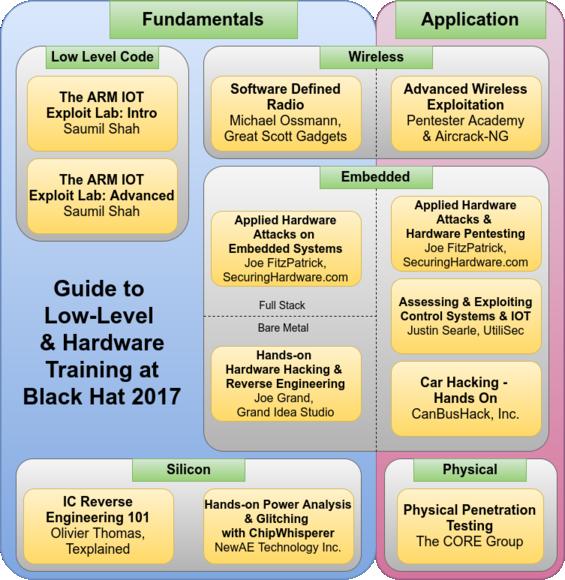
Blackhat Hardware Training Roadmap

Q3 review and Upcoming Training
Five years ago while I still worked on pre- and post-silicon penetration testing of CPUs, I began teaching internal courses on hardware security to functiona...

Hacker Summer Camp, 2016
Who's ready for Wrong Island Con/Black Hat/BsidesLV/Tiaracon/Defcon? I'm pretty sure I'm not, but that's not going to stop it from starting tomorrow! Here's ...

NSA Playset: SLOTSCREAMER, HALIBUTDUGOUT, and ALLOYVIPER for PCIe and Thunderbolt DMA attacks.
SLOTSCREAMER is an inexpensive device configured to access memory and IO, cross-platform and transparent to the OS - all by design with no 0-day needed. The ...

Hacking in Vegas, 2014...
Here's a rundown of what's happening in Las Vegas over the next week: Wednesday, Aug 6th: Techniques for Ensuring Secure Silicon applied to Open-Source Veril...

Timing Sidechannel Attacks for Hardware N00bs sells out at Bsides PDX and Bsides Seattle
20 Brave souls each in Portland and Seattle paid money and sacrificed a saturday morning to learn more about Timing Sidechannel Attacks for NOObs The whole w...

Timing Sidechannel Attacks for Hardware N00bs at DEFCON 21
Timing Sidechannel Attacks for NOObs was a success! The workshop was offered, for free, in the Hardware Hacking Village multiple times through the conference...

Hierarchy of Hardware Attacks
Generally, there is a very low barrier to entry when it comes to software or network-based attacks due to the fact that actual costs are minimal and most res...

Retail Hacking For Fun And Savings
Most technically inclined thrifty shoppers shop online. Thriftier ones know how to use the interweb to find the best online deals. But sometimes, you really ...

Hacking the Nikon WU-1a
Nikon makes some pretty sweet cameras but seem to be stuck in the dark ages with some of their accessories. The WT-# series of accessories cost over $1000 wi...
