In between the busyness of last fall, I had some insight into what 2018 would look like and how I and SecuringHardware.com could rise up to meet it. I’ve spent the past few years focusing on doing more of what works, less of what doesn’t, and filling every spare moment with trying new things. In that spirit, there’s a bunch of new things coming in 2018 that I’d like to sumarize.
New event
HardwareSecurity.Traing in San Francisco last fall went so well, we decided to repeat the model elsewhere. We’ve got an event planned for Berlin in March and Rockville, MD in April. Both follow the same format of having several hardware trainings co-located with a guess technical presentation at lunch time.
SecurityTraining.Berlin will be held at Deutsche Telekom in Berlin on 19-22 March
HardwareSecurity.training will be held in Rockville, MD 23-26 April
New Class
One of many great discussions with other trainers that came out of HardawreSecurity.Training is that we all encounter attendees that either 1) only want an overview of the content we deliver or 2) have trouble expressing to their management the true implications of the tools and techniques that they learin in our trainings.
In order to accomodate both these requests, we collaborated develop and deliver a brand new class titled Hardware Attacks, Threats, Risks, and Mitigations:
By giving a sample of all the different topics we each cover in depth in our own classes, this course provides a high-level, comprehensive survey of the state-of-the-art in hardware attacks, threats, and risks. From the system level all the way down to the silicon level, attendees will be exposed to the many attack vectors within the hardware security landscape. Unique hands-on exercises using pen-and-paper will lead into group discussion of the implications, impact, and risk mitigation for each type of attack. Emphasis will be placed on the problem solving and hardware implications, not on in depth hardware setup or exhaustive coding of solutions.
New Gear
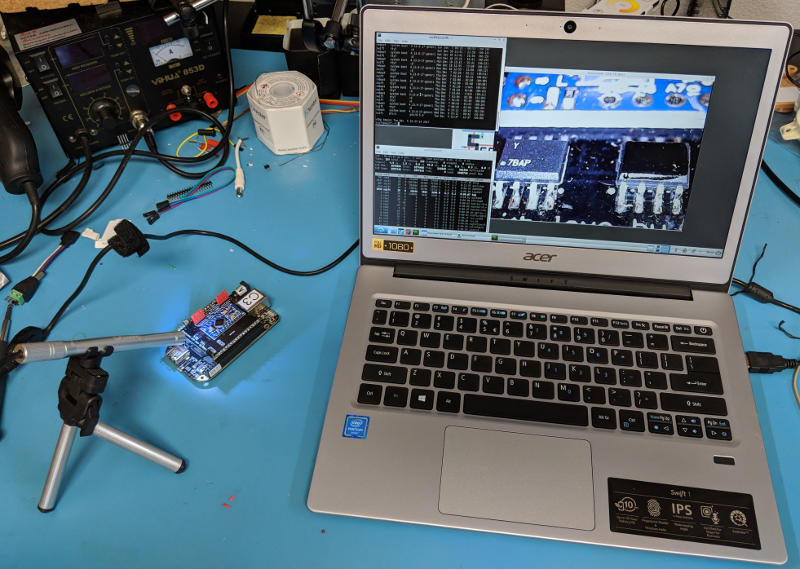
Instead of fighting VMs or Toolchains for the first few hours of every class, I started collecting Acer Chromebooks for class use. I have been amazed how budget laptops from 2013 have held up, but it’s finally time to replace the whole lot.
The current generation Acer Swift 1 turns out to be a winner, since it meets every requirement while still being affordable when purchased by the dozen:
| c720 | Swift 1 | Benefit |
|---|---|---|
| Celeron 2955u | Pentium N4200 | Up to double performance, lower power and fanless |
| GalliumOS | Lubunutu | mainstream hardware all supported out of the box |
| 2GB DRAM | 4GB DRAM | Plently of memory, Longer logic analyzer captures |
| 2 USB ports | 4 USB ports | No more hubs, plus USB power cables |
| 11.6” HD TN Panel | 13.3” FHD IPS Screen | Bigger, brighter, higher resolution with better viewing angles |
| 2.8 lbs | 3.0 lbs | Every ounce matters when you ship 24 of these, but the difference is made up for with fewer USB power cables! |
I also added USB microscopes to every kit. After seeing them in use for the first time last month, I apologize for not getting them years ago!
Upcoming Training
Registration is open for CanSecWest, SecurityTraining.Berlin, HardwareSecurity.Training, Infosec in the City, and Black Hat:
Don’t see what you want? Inquire about booking private training!