
A Measured Response to a Grain of Rice

Joe FitzPatrick
@securelyfitz
15+ years of hardware fun:
• silicon debug
• security research
• pen testing of CPUs
• security training
SecuringHardware.com:
• Applied Physical Attacks Training
• HardwareSecurity.Training
Disclaimers!

What is a Hardware Implant?

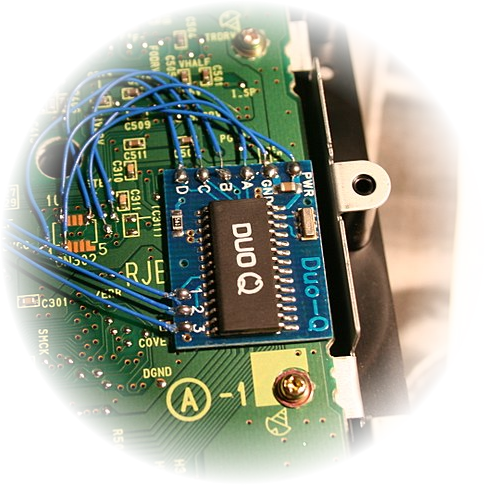
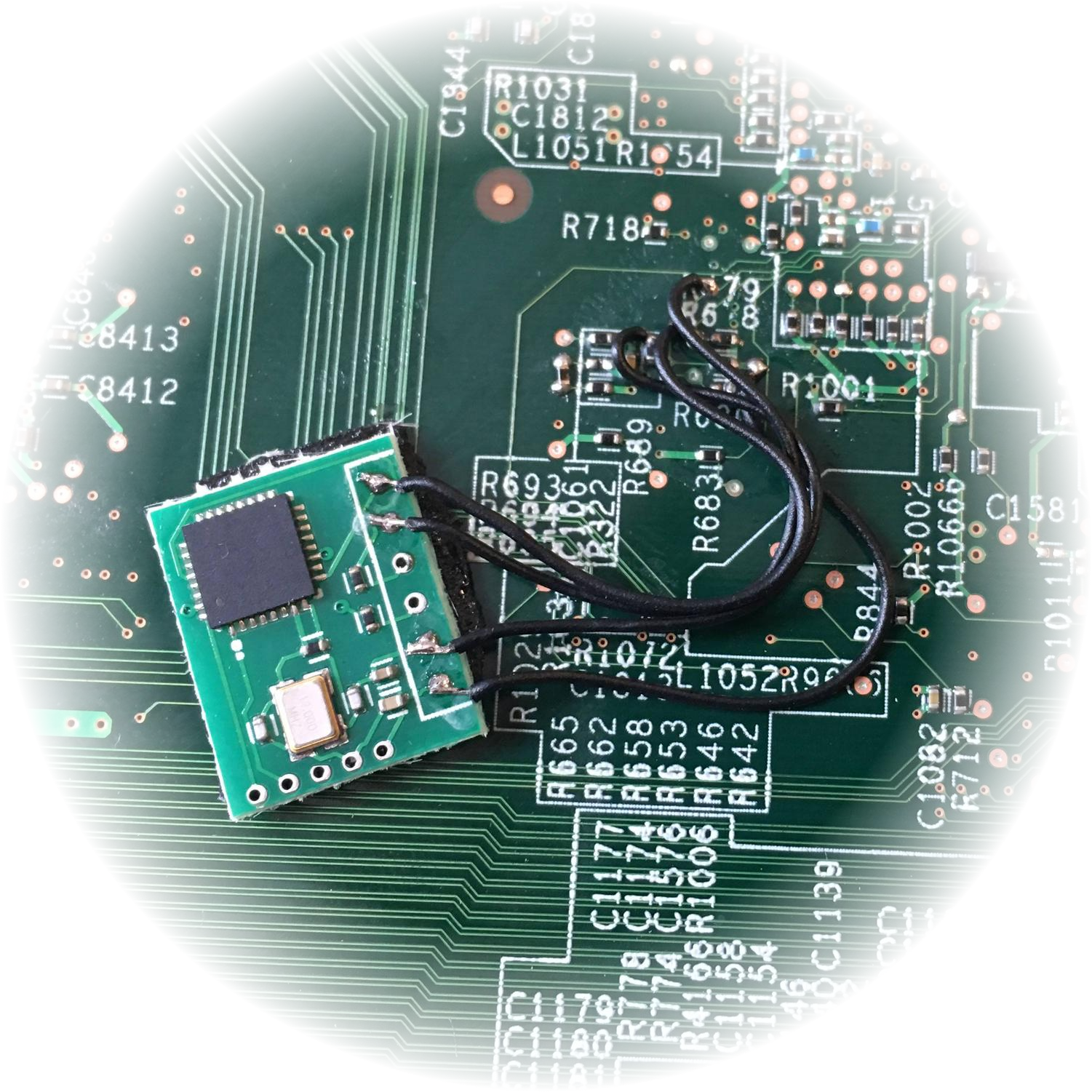

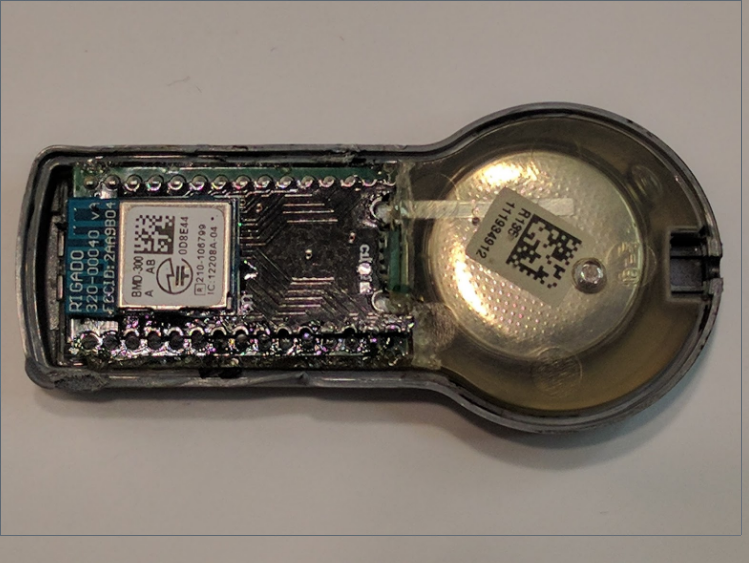

Evolution of USB hardware attacks

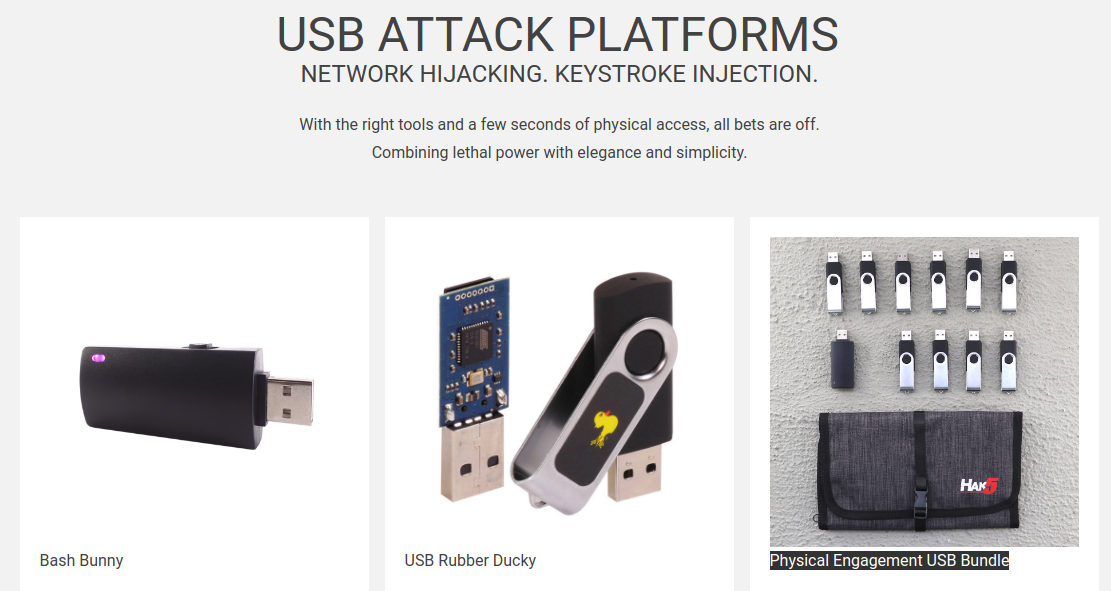
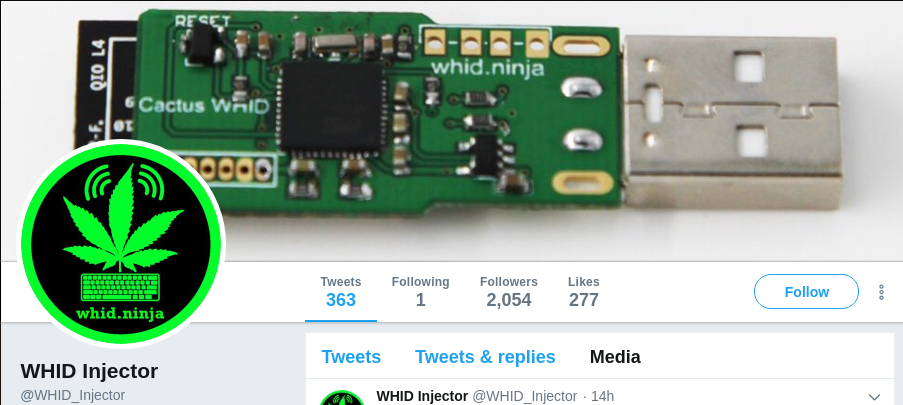


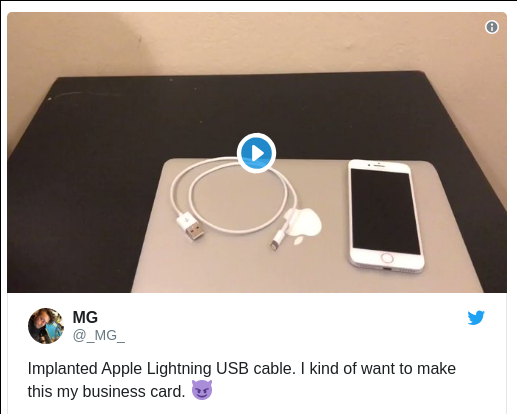
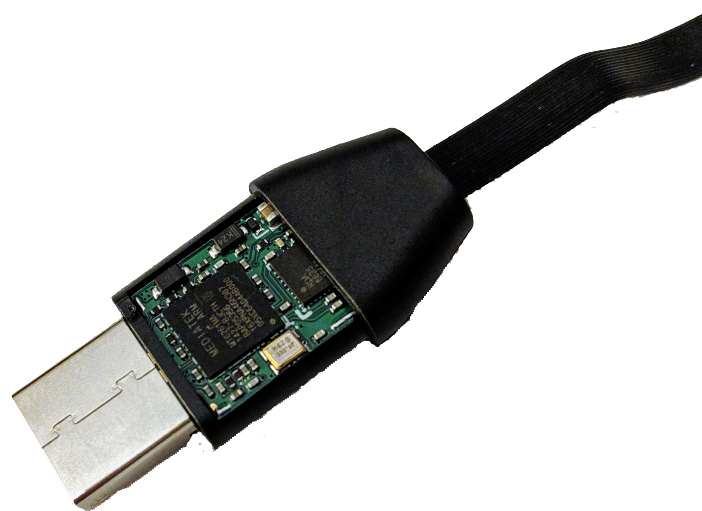
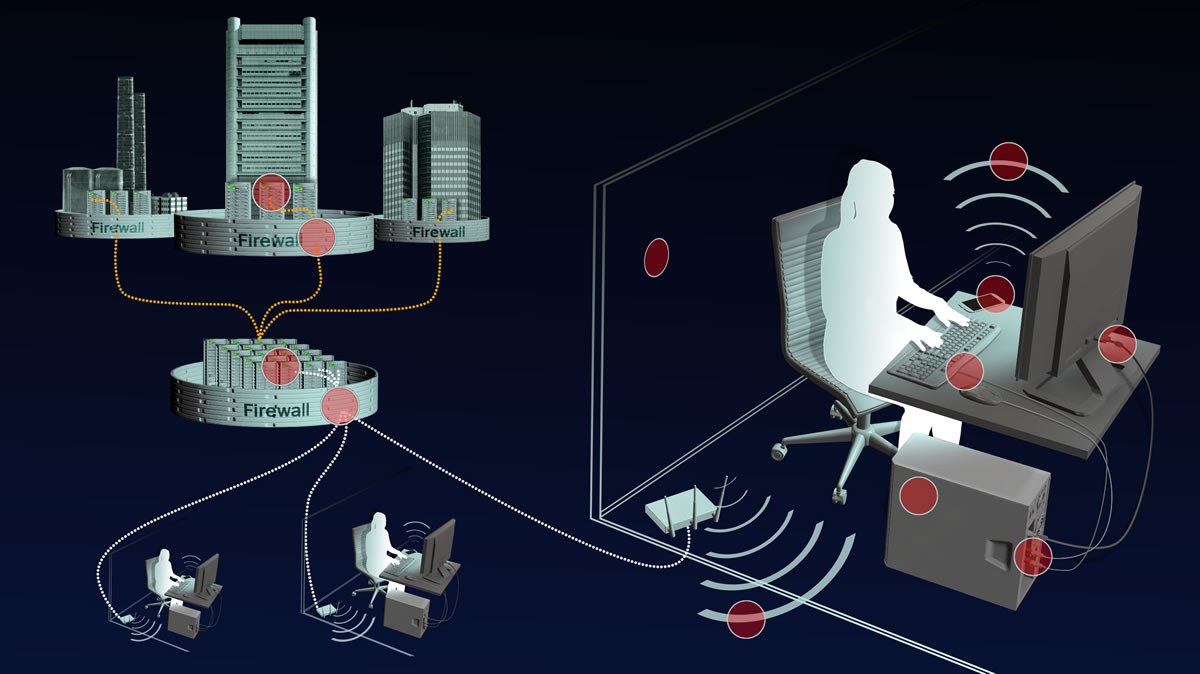
How do we connect a Hardware Implant?
When do Hardware Attacks make sense?
Why is this relevant?


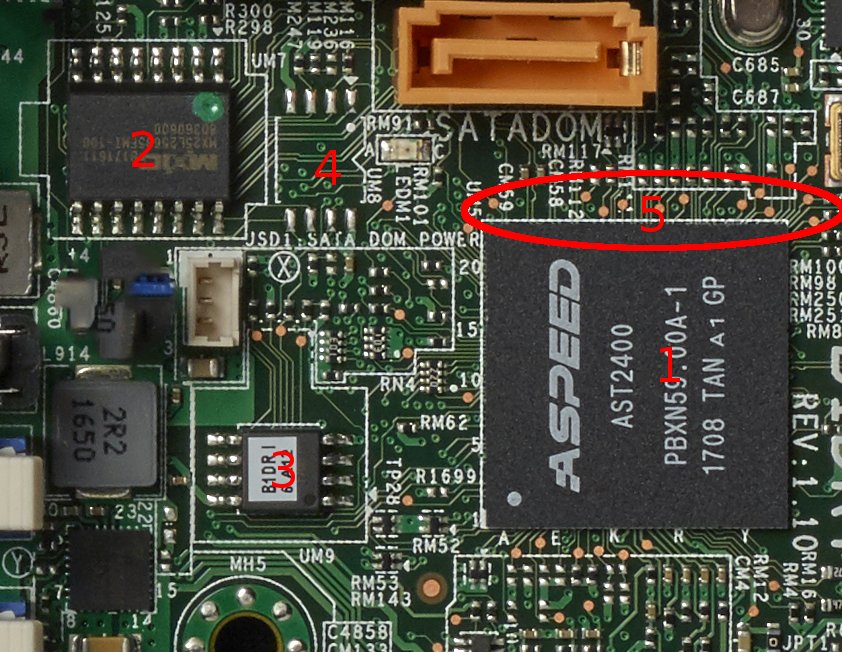
Hardware Indicators of Compromise
YES!
That's how they're made!
NO?
ECOs, updates and revisions guarantee that
YES?!
THEY ALL DO THESE DAYS
We still don't know!
Component Grafitti?
Should we trust anyone who says they do?
Is this real?
YES


YES
But that's not the quesiton

But I'm not the only one
Expect lots of homebrew solutions at BH USA, DEFCON, and in upcoming PoC||GTFO
How did we get here?
• Hardware vulnerability
• Software expliotable
• REAL response
They don't know they shouldn't.
Taking a measured response...
You can look for it
That will distract you
What should we worrry about?
All for money and disruption
What can we do about it?
Then why worry about 1M€ attacks?
How common is that attack?
Risk = vulnerability * exposure
So What?
Hardware Attacks are a real threat...
...respond to the threat, not the hype
A Measured Response to a Grain of Rice
Joe FitzPatrick - @securelyfitz - joefitz@securinghardware.com