
0
Anatomy & Impact of Hardware Attacks

Joe FitzPatrick
@securelyfitz
15+ years of hardware fun:
• silicon debug
• security research
• pen testing of CPUs
• security training
SecuringHardware.com:
• Applied Physical Attacks Training
• HardwareSecurity.Training
1
Hardwhat?
4
is harder than software
has longer development cycles
gets fewer development iterations
has real tangible costs
are riskier to deploy
have nonzero risk of bricking
just don't scale
Ignorance to hardware vulnerabilities
General laziness (aka efficiency)
Massive *percieved* barrier to entry
7
What is a hardware attack?
Attacks that require physical access
• Physical Modifcations
• Invasive or noninvasive observation
• Hardware MITM devices
Attacks on hardware physics and logic
• Observation of sidechannels
• Altering and glitching inputs
Attacks on hardware architecture
• Logical bugs in silicon implementations
• Subverting silicon features maliciously
Hardware-enabled software attacks
• Physical access changes software behaviour
• Physical access informs a software attack
Software-enabled hardware attacks
• Software subversion of hardware devices
• Software accessible hardware flaws
10
Make Hardware do the Hard work
Fun prank?
Off the shelf tools
vs.
explicit trust in hardware
Simple pentest?
Use Physical Accessto inform
the Software Attack
Red team engagement?
You don't need to be a nation state target
to be a hardware attack victim!
Organized campaign?
multiple hops through different systems
vs.
targeted hardware implant
12
Why Hardware?
18
What can we do with physical access?
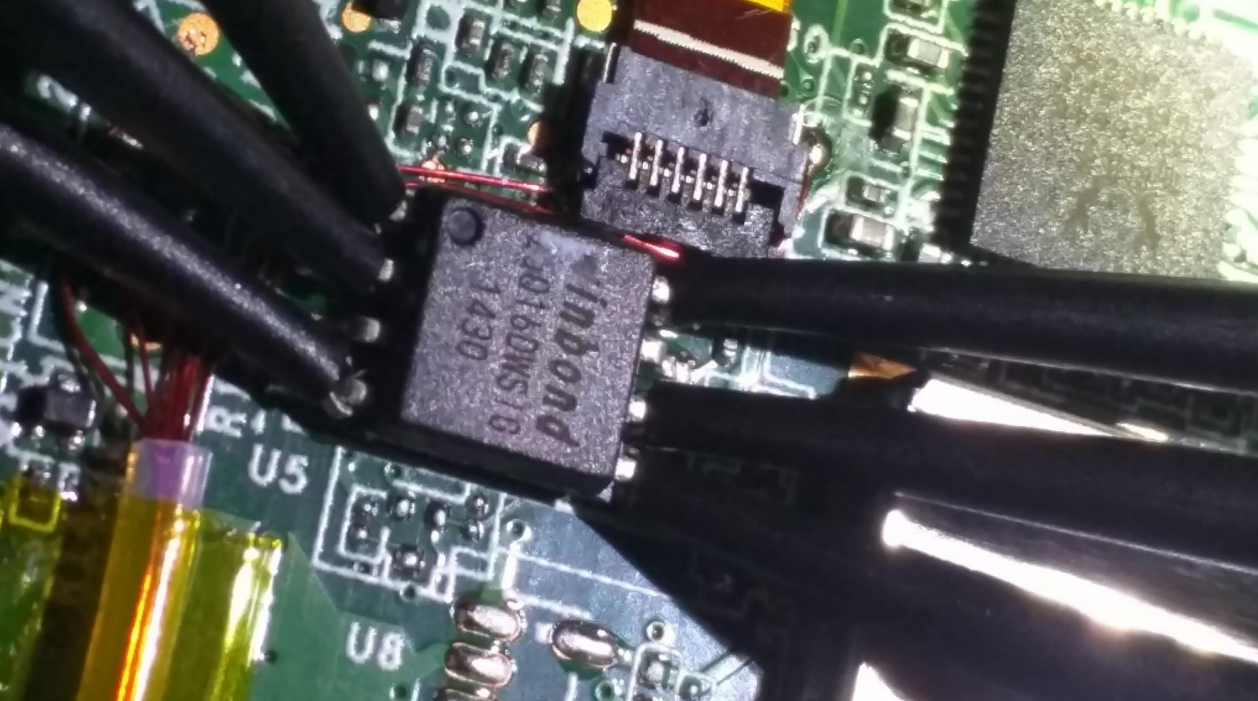
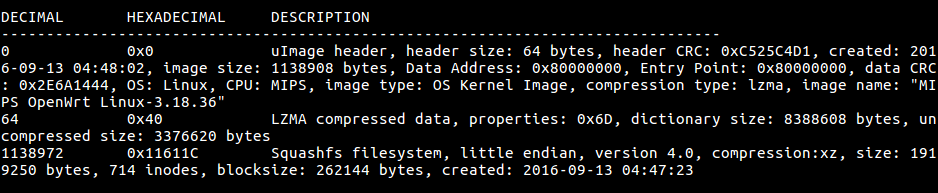
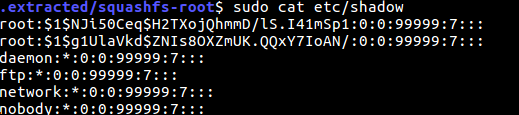
23
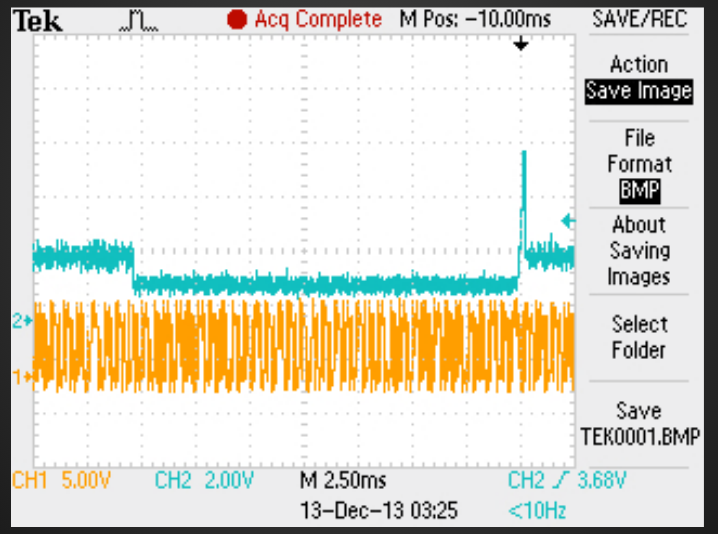
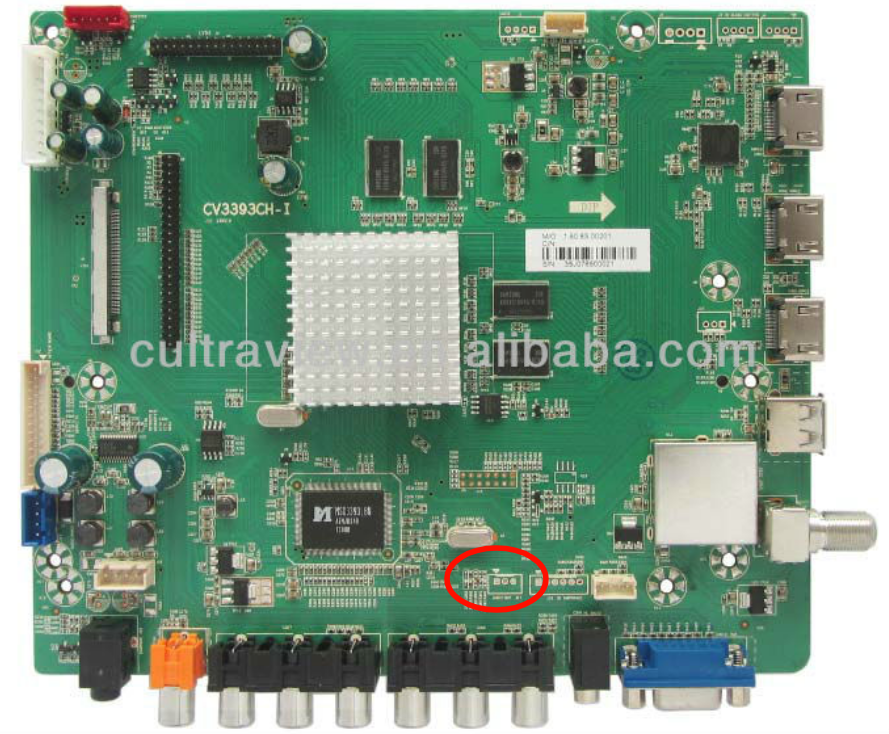
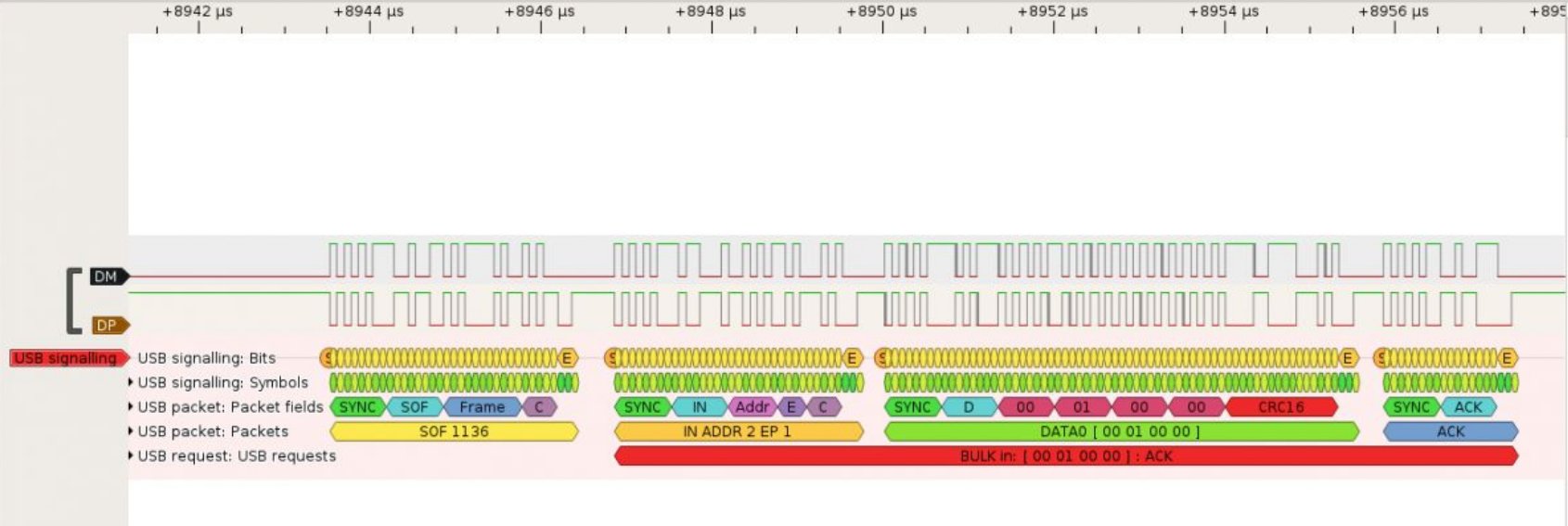
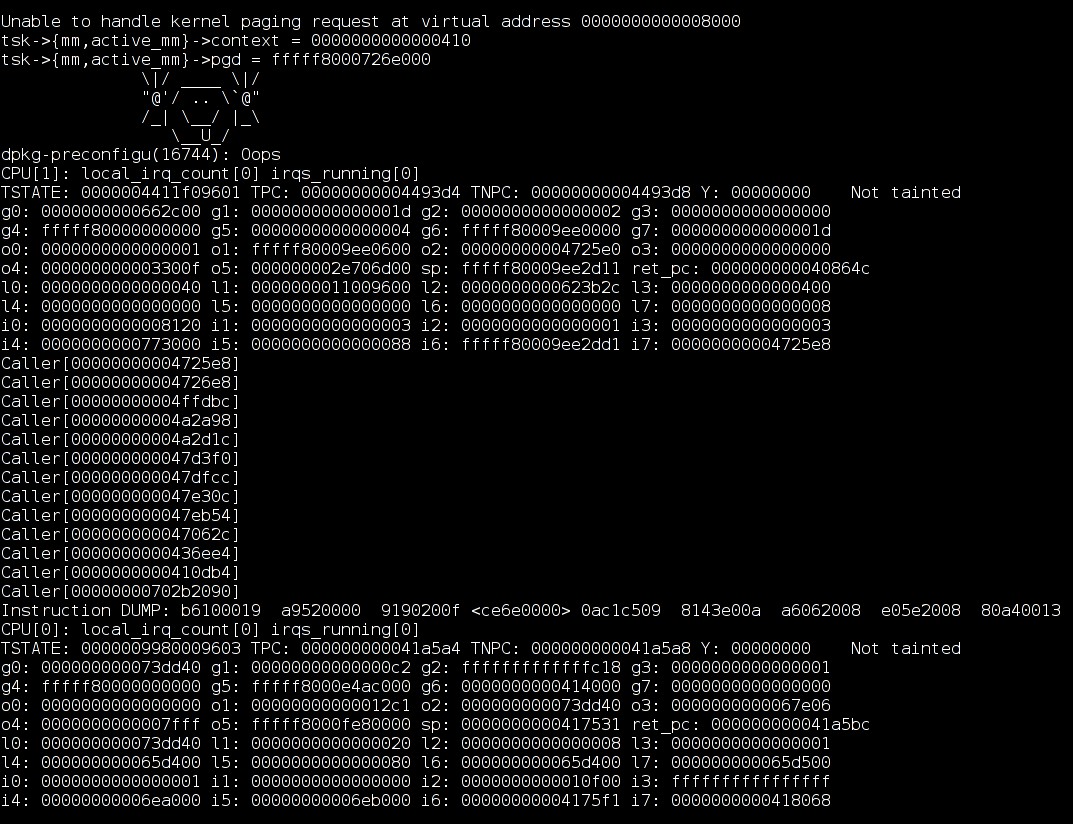
What else can we get with physical access?


30
USB: Hardware Attacks with Safety Gloves On
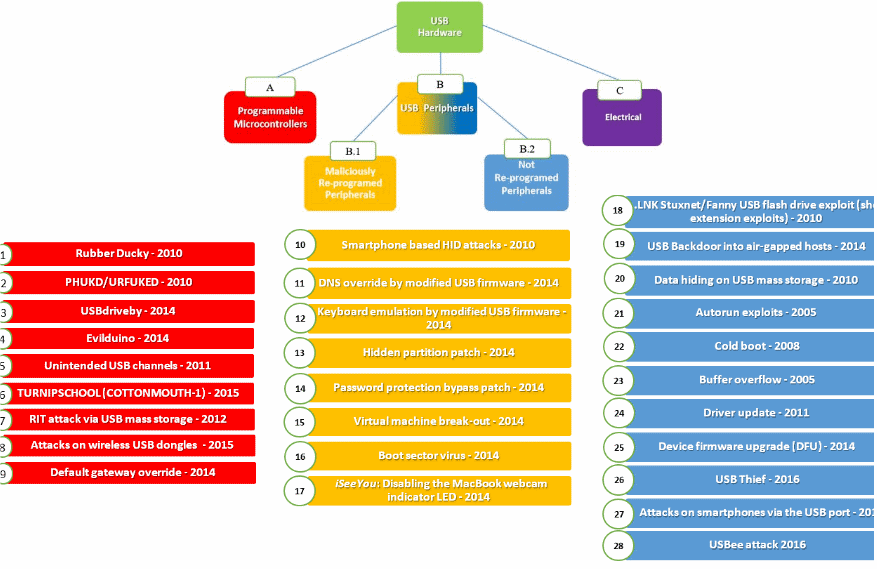
Malicious hardware device
Malicious firmware on exsiting device
Malicious payload on a normal device
Malicious electrical attacks
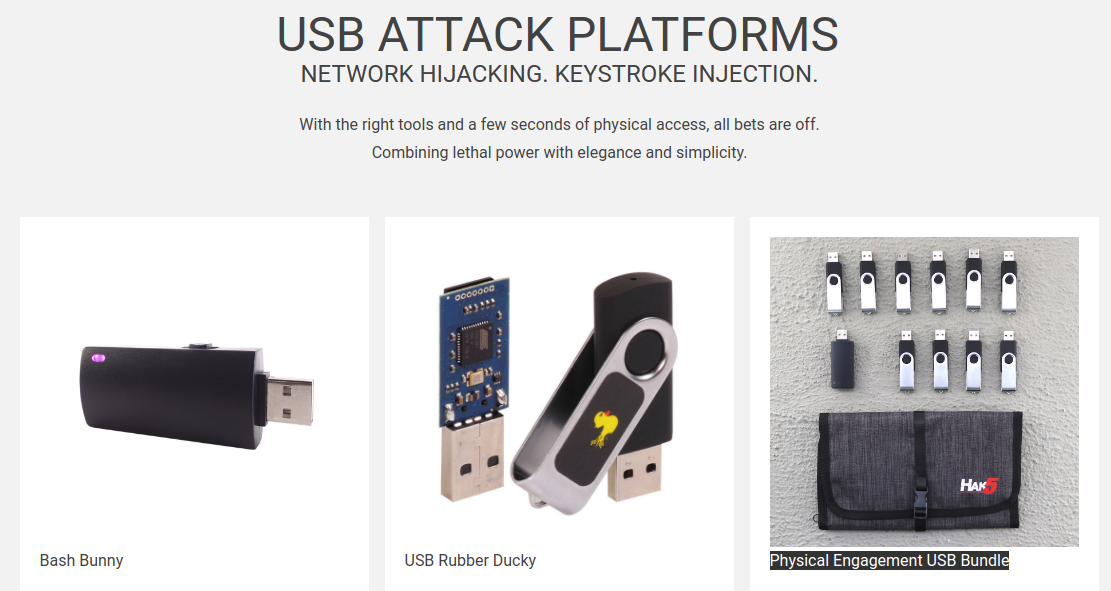

You'll learn more than you expect
34
Attacking the Fancy Interfaces
It's running 2.5 to 8GHz
It's locked up inside your PC
It's not like hooking wires up to a parallel port!

It automatically connects and negotiates
It has LOTS of error checking/correction
FPGAs can do it out-of-the-box*
Thunderbolt can do it too!
1. Connect everything inside your PC
2. Lock it in a box
3. Call it secure...

Think about 386 paged memory.
Think about embedded graphics.
Think about IP blocks on an SOC.
Hot swap predates thunderbolt.
Even systems that don't support hot swap - support hot swap

How about 3 wires:

40
A Softer, Gentle Hardware Attack?
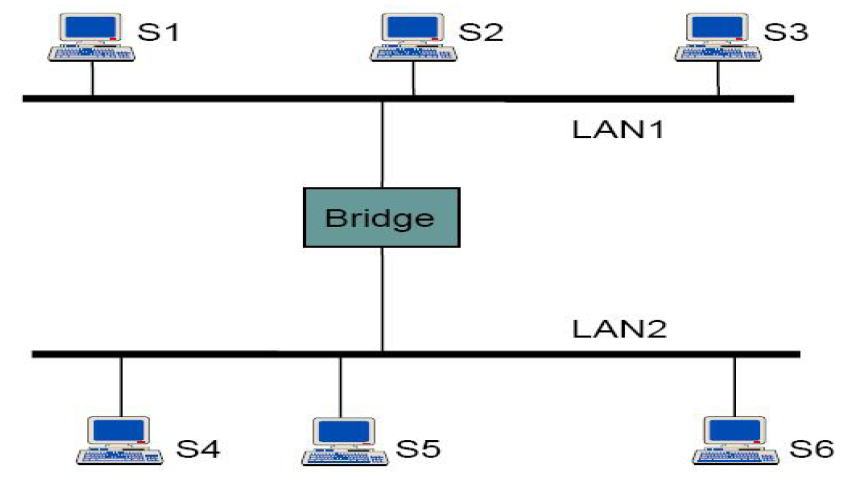
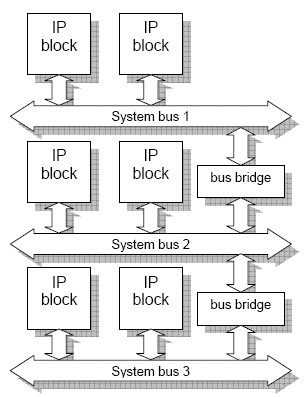
Why should we treat them any differently?
Attacking software is finding and subverting the flaws in he abstractions
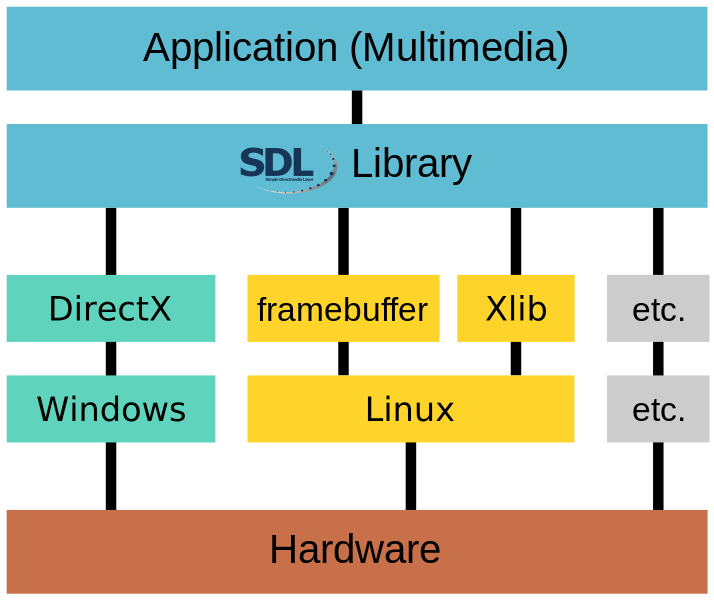
44
Hardware attacks are not difficult
Software can access hardware!
Physical access is not a high barrier
You don't need malicious hardware to have a hardware attack!
48
So What?
Software is just the tip of the iceberg.
Don't ingore the hardware underneath!
Anatomy & Impact of Hardware Attacks
Joe FitzPatrick - @securelyfitz - joefitz@securinghardware.com