
1
Waiting for
IOT Security
A Beckett-Inspired Tragicomedy, in 3 Acts

Joe FitzPatrick
@securelyfitz
15+ years of hardware fun:
• silicon debug
• security research
• pen testing of CPUs
• security training
SecuringHardware.com:
• Applied Physical Attacks Training
• HardwareSecurity.Training
Disclaimers
No IOT Security experience requiredThis presentation contains spoilers
Spoiler: nothing happens, there's nothing to actually spoil
Act 1
25

Samuel Beckett, IOT Startup Coach
"Ever tried. Ever failed. No matter. Try again. Fail again. Fail better."
"Try again. Fail again. Better again. Or better worse. Fail worse again. Still worse again."
27
The path of Innovation
Vladimir, IOT Startup CISO

Well? What do we do?
Estragon, IOT Startup CEO

Don't let's do anything. It's safer.
34
Brief History of Computing
1800

1940's - Harvard Mark 1

1950's - SEAC - Delay line memory
6 inches = 1 ns
18 Gbps HDMI2 cable = 36 bits/ft
45 miles = 1 megabyte
1950's - IBM 701 - Core Memory

1960's - IBM system 360

1960's - Grace Hopper at UNIVAC
1960's - RTL Logic NOR gate

1960's - Code for Apollo mission


1970's - Hobbyist and Kit Computers
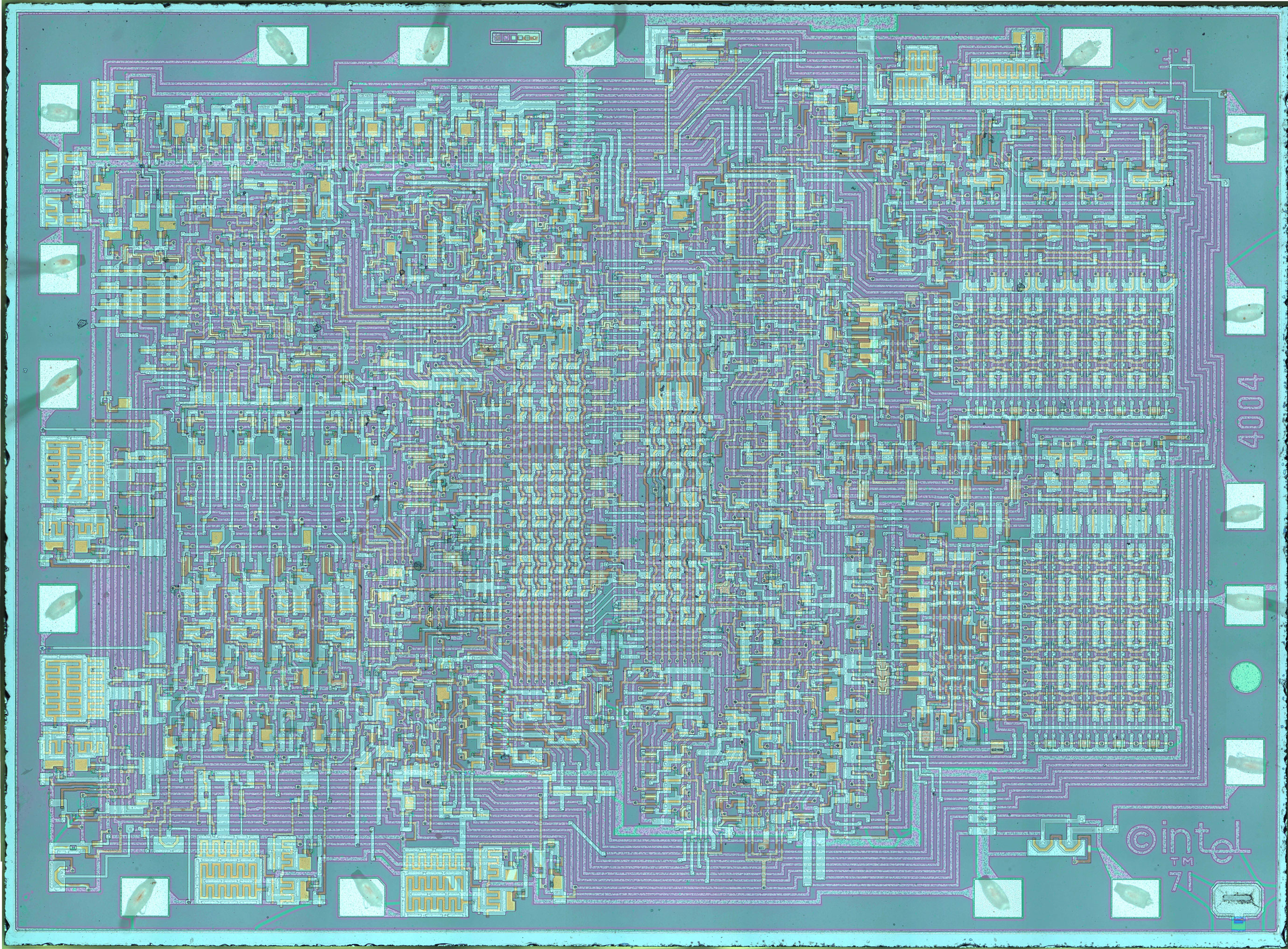
1970's - Microprocessors

1980's - Personal Computers
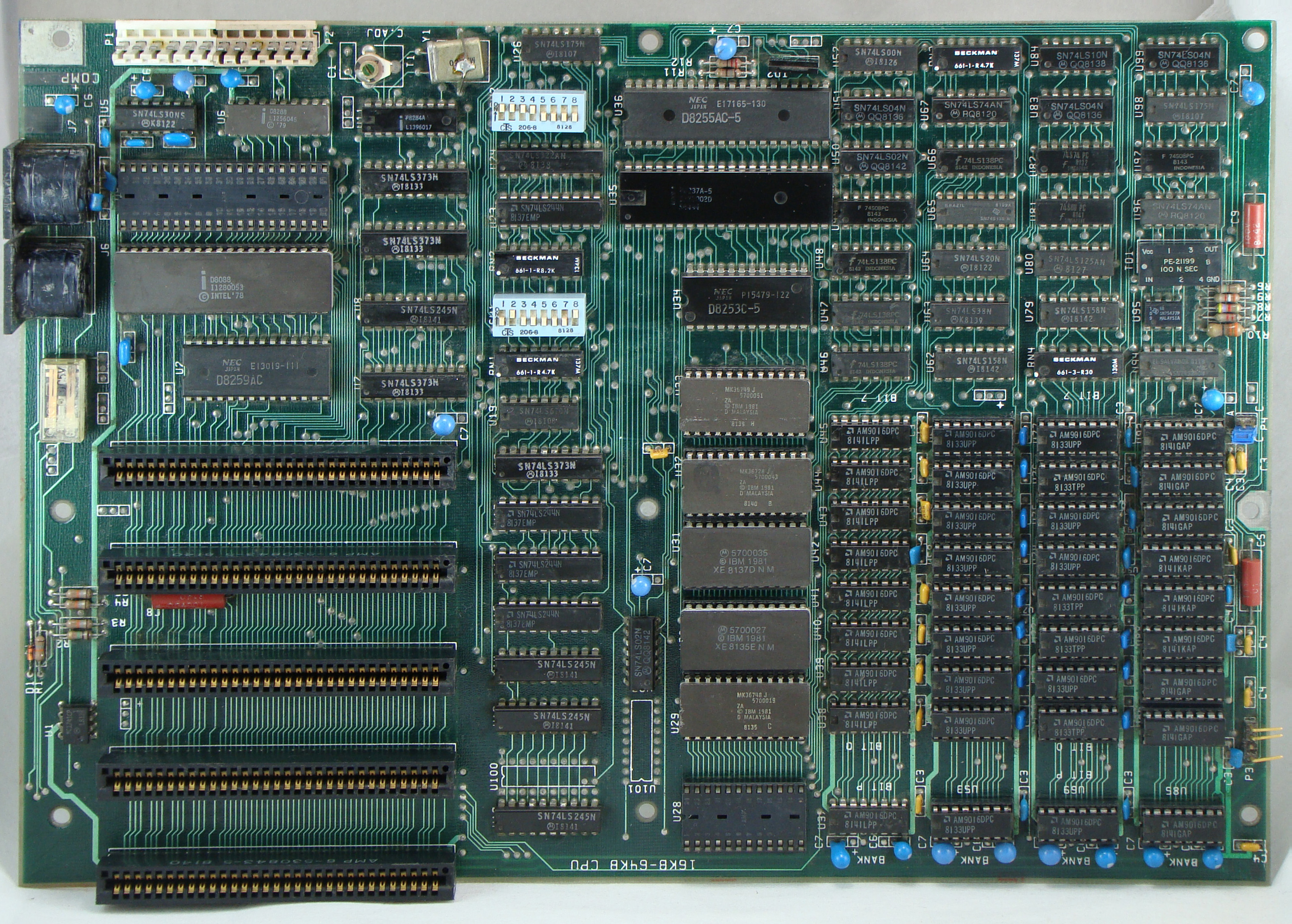
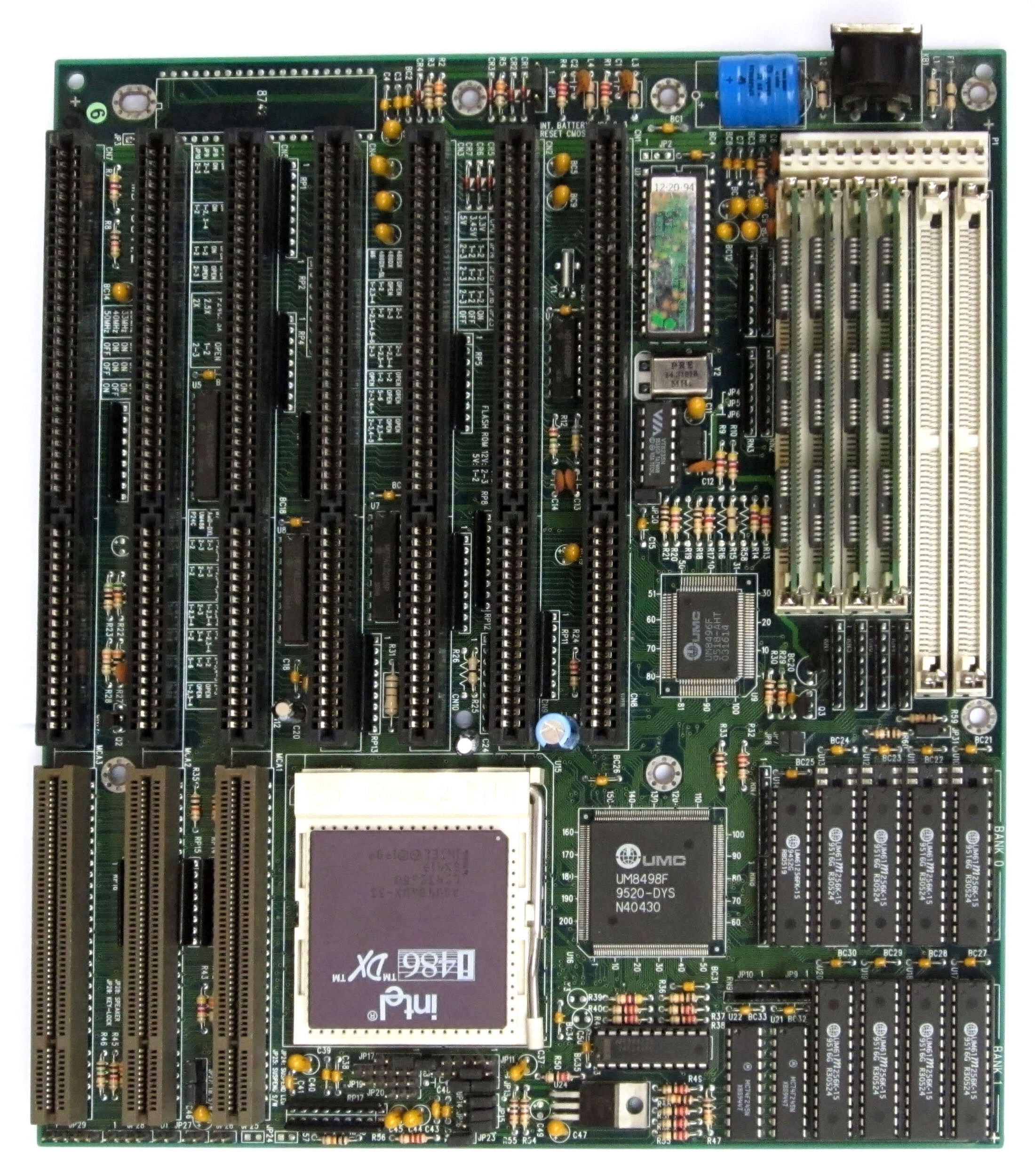
1980's - Flat Memory, Paging & More

1990's
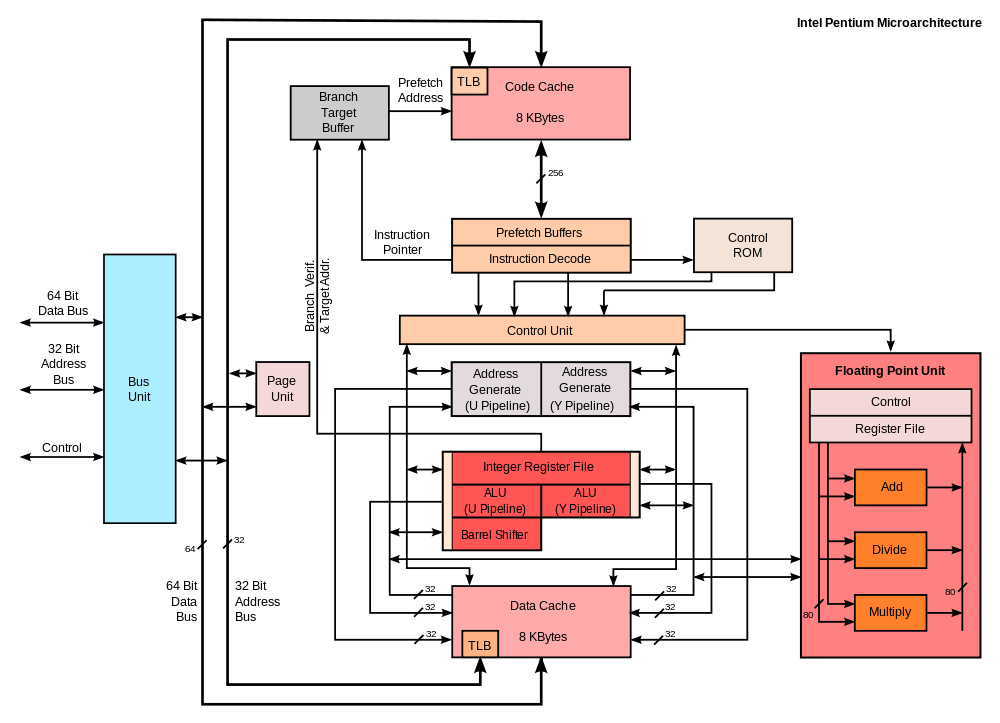
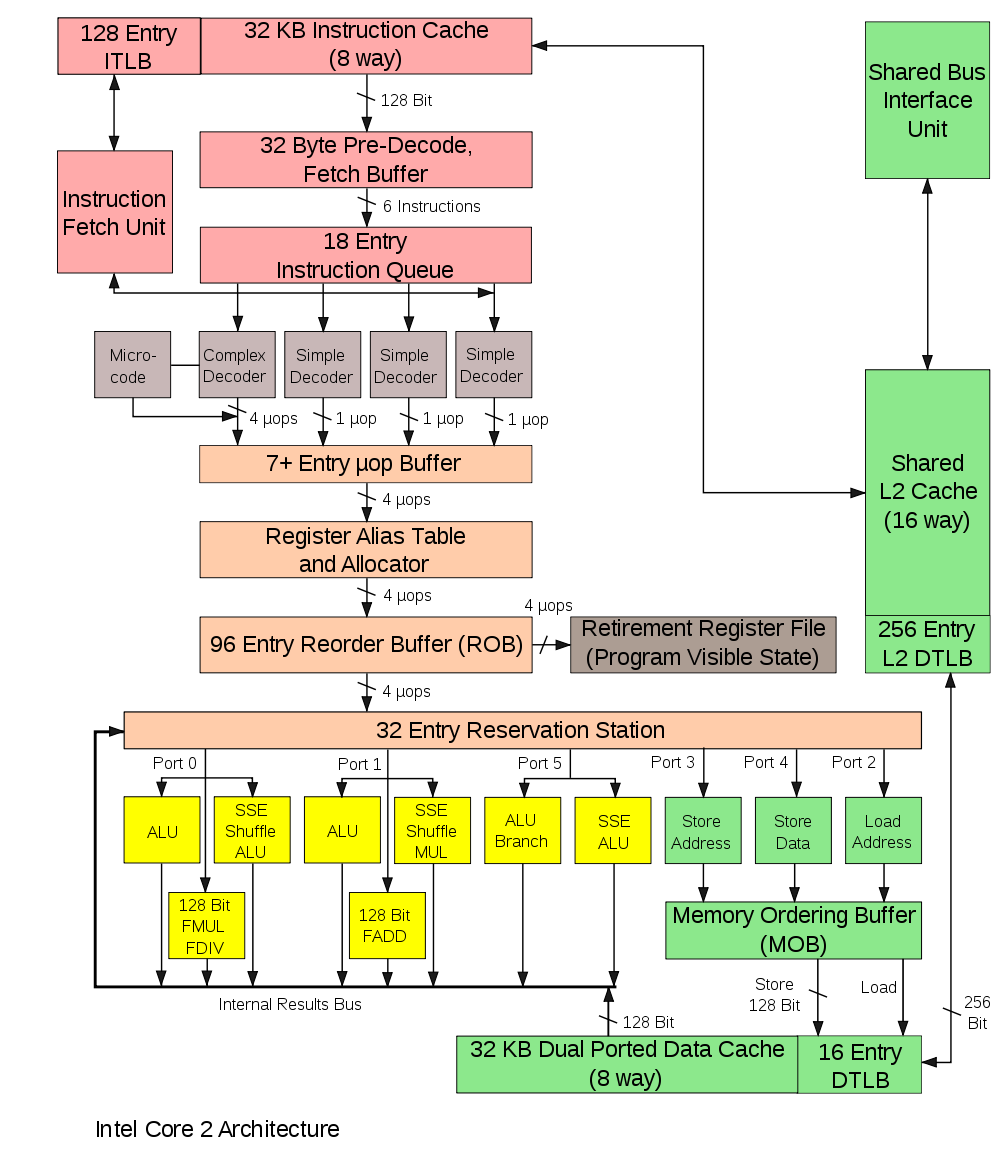
1990's - OOE and Superscalar Processing
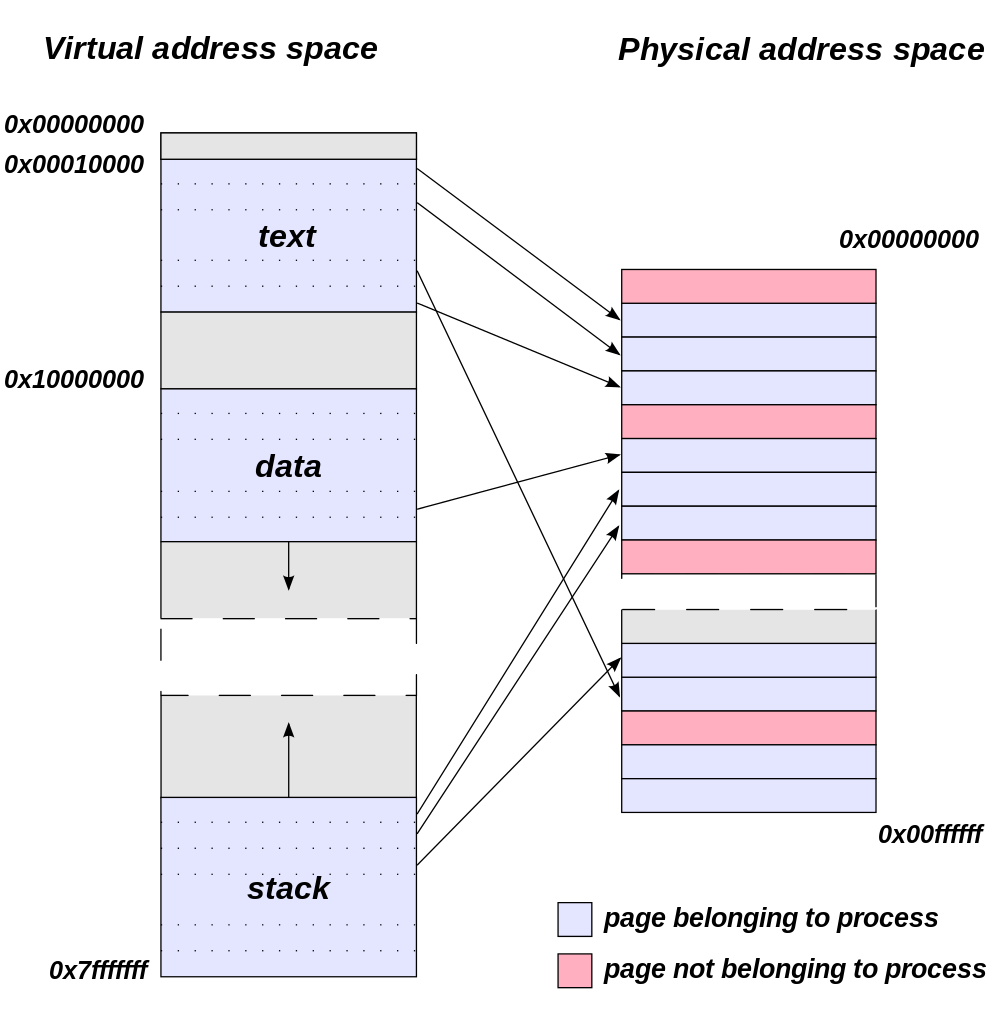
1990's - Process Isolation, Preemtive Multitasking
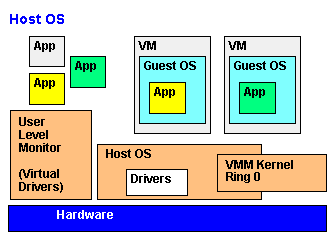
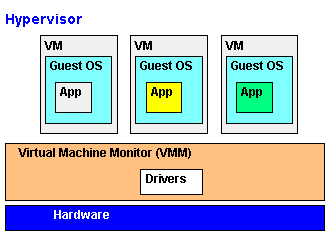
2000's - Hardware Virtualization, DEP and ASLR
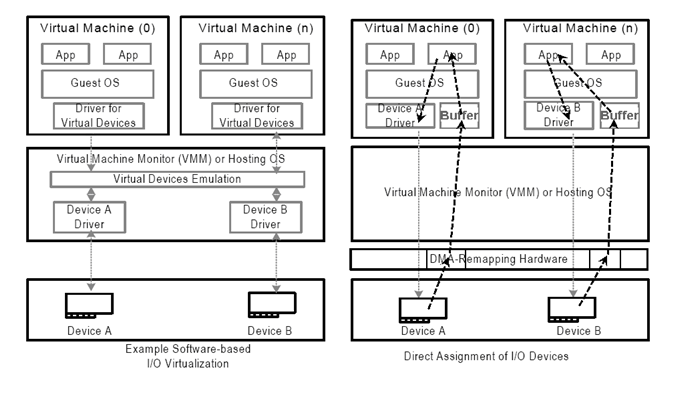
2000's - IO Virtualization

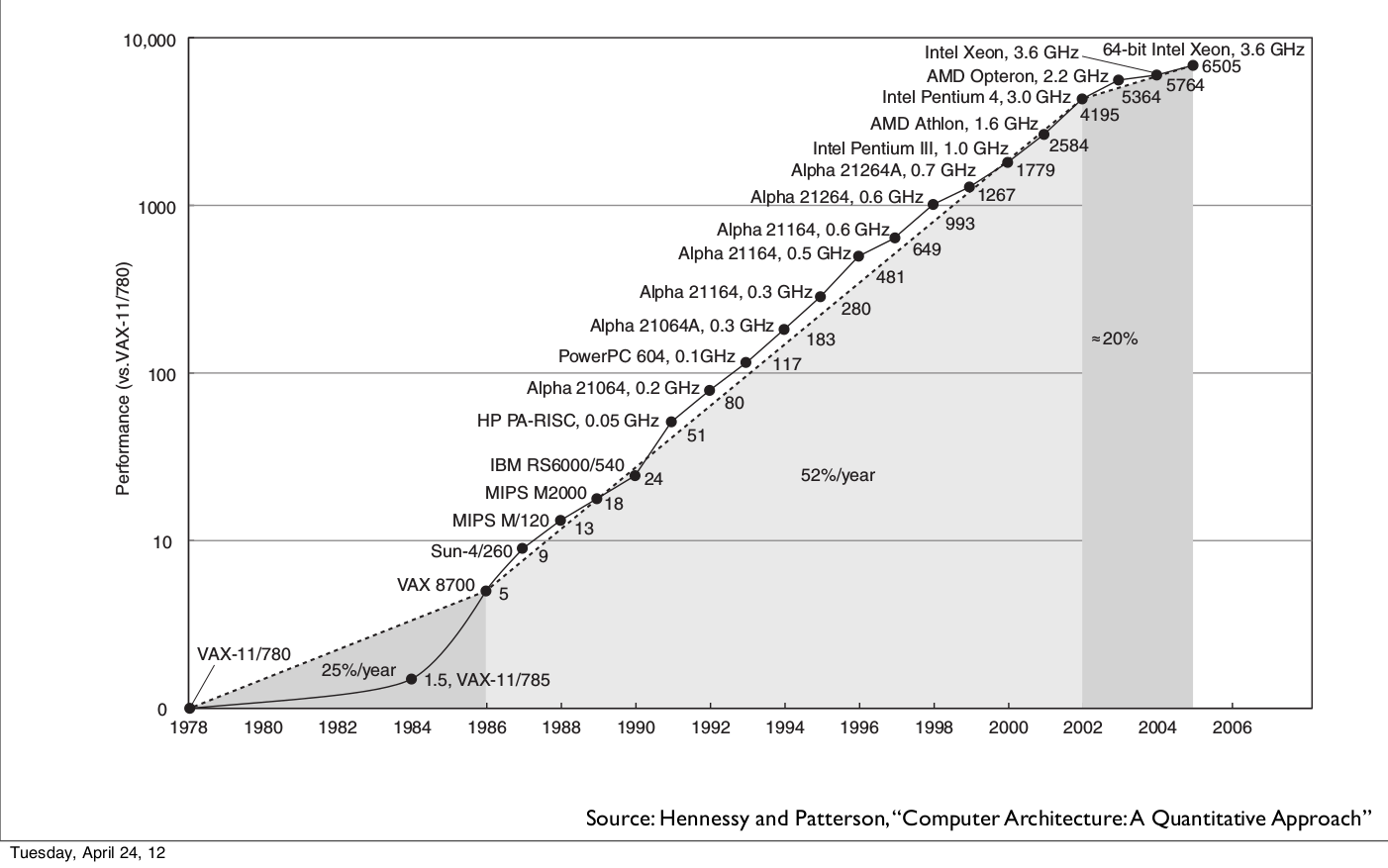
2010's - Cloud Everything, CPU Cycles to Spare
Vladimir, IOT Startup CISO

What do we do now?
Estragon, IOT Startup CEO

Wait.
Yes, but while waiting.
What about hanging ourselves?
Act 2
44
What is IOT Security?

“...[IOT Security] is a dramatic vacuum. Pity the [hacker] who seeks a chink in its armour, for it is all chink. It has no plot, no climax, no denouement; no beginning, no middle, and no end… [IOT Security] frankly jettisons everything by which we recognize [Security]...
Kenneth Tynan [with liberties]
The Observer, 1955
”
Hierarchy of Computing Needs
46
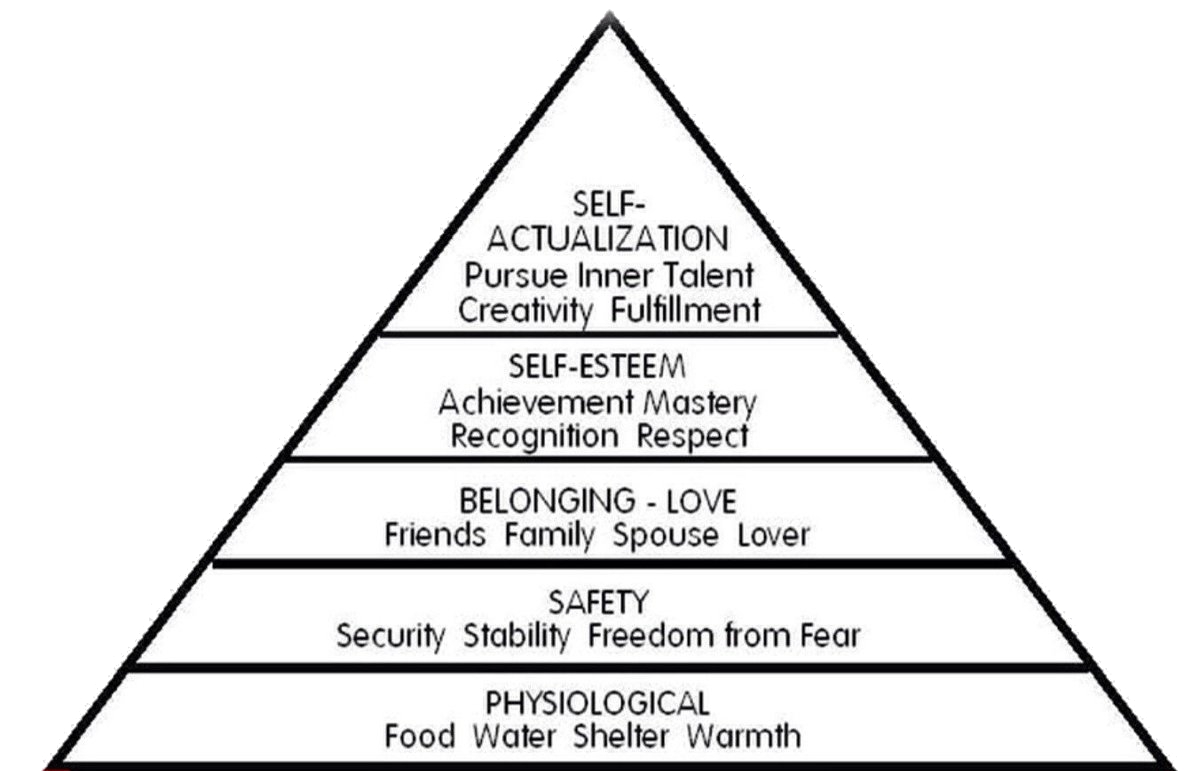
Where do Computers Fit?
Functionality
Turing Completeness
RISC vs CISC
Hardware acceleration:
Floating point
Cryptography
Performance
Moore’s Law
Performance per square foot
Performance per dollar
Performance per watt
Usability
Line Printers
Keyboards
Screens
CLIs
Mice
GUIs
UX
Touchscreen LCDs
Reliability
MTBF
Exception handling
ECC storage
RAID
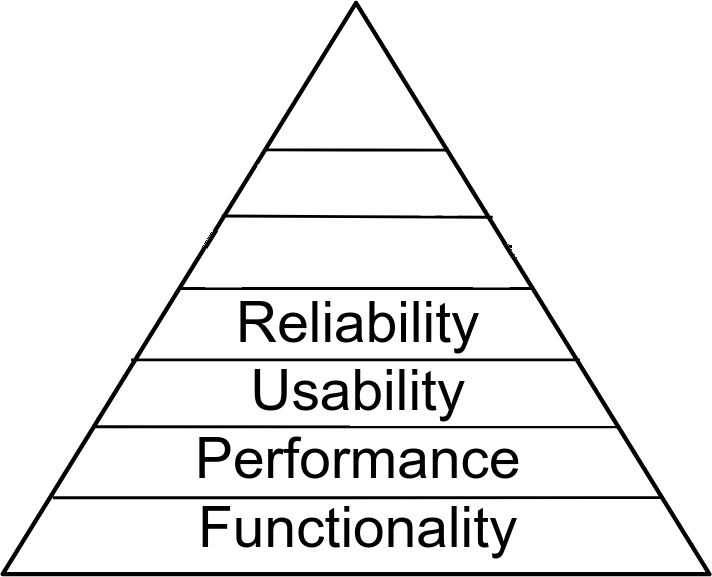
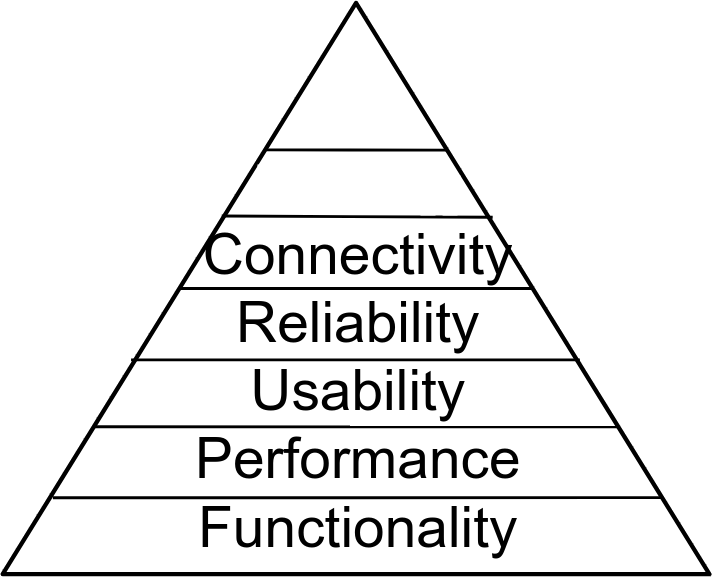
Connectivity
Modemsa
Ethernet
Wifi
4G
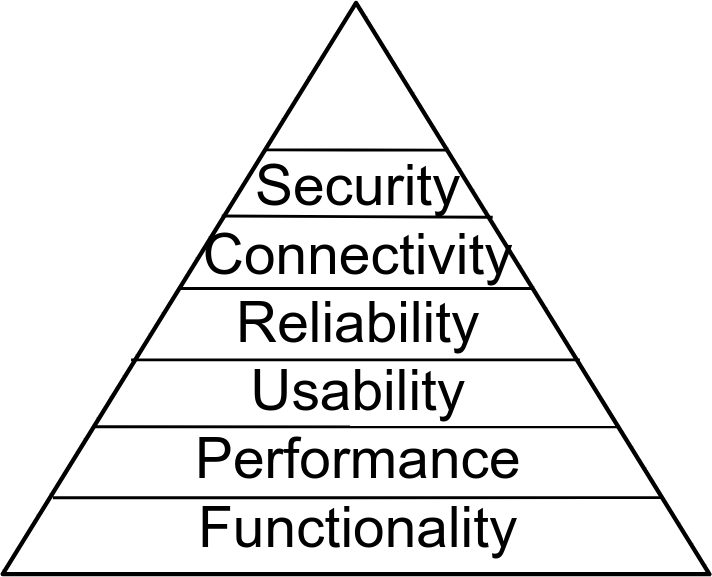
Security?
Virtual Memory
DEP
ASLR
Virtualization
Hardware RNGs?
Accelerated Crypto
Vladimir, IOT Startup CISO

Words words. Speak.
@securelyfitz, IOT Security Cynic

[IOT Security] told me to tell you [it] won't come this evening but surely tomorrow.
Is that all?
Yes Sir.
You work [on IOT Security]?
Yes Sir.
What do you do?
I mind the goats, sir.
Hierarchy of Computing Needs
55
What About ICS?
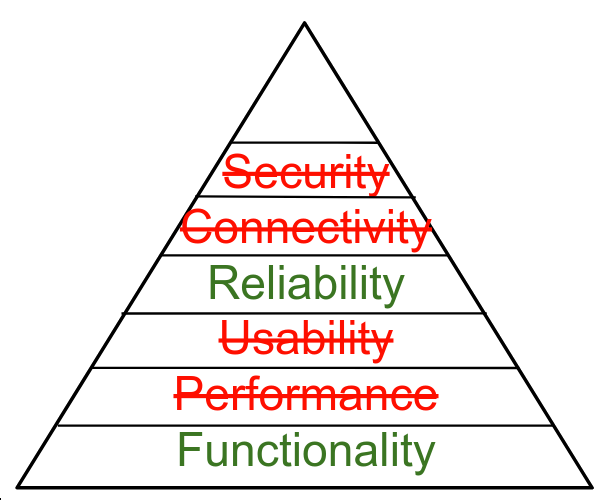
What About Medical Devices?
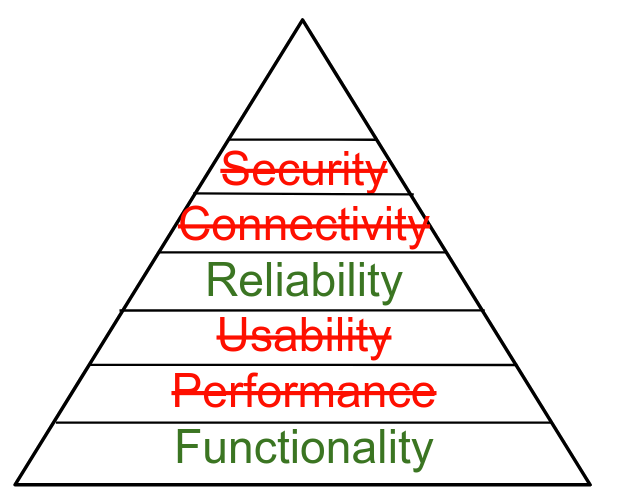
What About Mobile Devices?
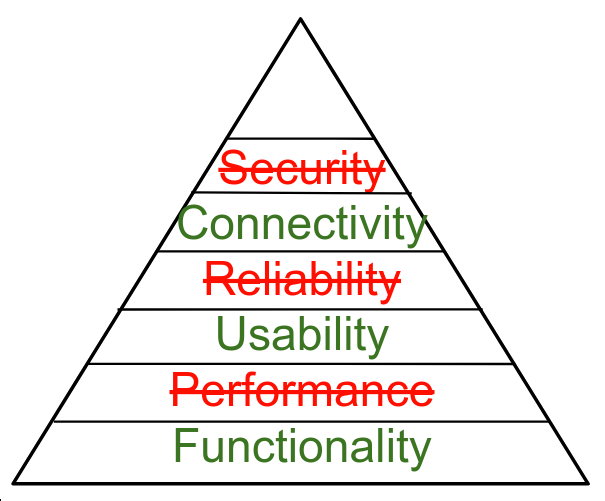
What About IOT?
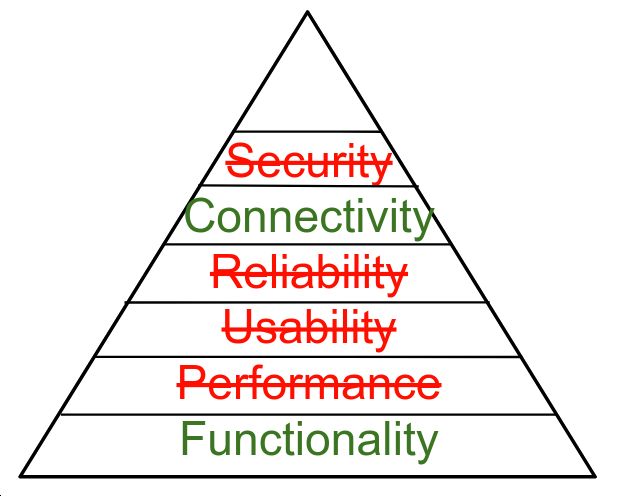


[What] is [IOT Security]?
[IOT Security]?
You took me for [IOT Security].
Oh no, Sir, not for an instant, Sir.
[What] is [IOT Secuirty]?
Oh [it's] a... a kind of acquaintance.
Nothing of the kind, we hardly know [it].
True... we don't know [it] very well... but all the same...
Personally, I wouldn't even know [IOT Security] if I saw [it].
IOT Threat Landscape
00
...and the full attack surface and complications of full stack OSs.
...and the full attack surface and complications of connected devices.
...and the full attack surface and complications of that potentially personal information.
...and the full attack surface and complications of kinetic threats.
...and the full attack surface and complications of physical access.
...and the full attack surface and complications of rushed and incomplete implementations.
...and the full attack surface and complications of legacy and unsupported devices.

Let us not then speak ill of our generation, it is not any unhappier than its predecessors.
Let us not speak well of it either.
Let us not speak of it at all.
Act 3?
08
What is IOT Security?

“If I knew, I would have said so in the play”
10
How long do we wait?
We don’t care about security until we:
1. Learn we don’t have it
2. Have the capacity to solve it
We could wait until mainstream computing's security level catches up...
...maybe that's tomorrow?
...maybe all the old attacks are new again?
Estragon, IOT Startup CEO

And if we dropped [IOT Security]? If we droped [it]?
Vladimir, IOT Startup CISO

[IOT Security] would punish us.
13
IOT Design for Security
We could be proactive and lead the way:
• Document our security expectations.
• Minimize attack surface
• Respond constructively to security reports.
• Apply mainstream best practices to IOT devices
• Insist on it as producers and consumers
Vladimir, Bay-area, homeless, IOT Startup has-been, on DFS

It's too much for one [person].
On the other hand, what's the good of losing heart now, that's what I say.
We should have thought of [security] a million years ago, in the nineties.
Waiting for
IOT Security
A Beckett-Inspired Tragicomedy, in 3 Acts
Joe FitzPatrick - @securelyfitz - joefitz@securinghardware.com