
1
The Hardware Pivot

Joe FitzPatrick
@securelyfitz
15+ years of hardware fun:
• silicon debug
• security research
• pen testing of CPUs
• security training
SecuringHardware.com:
• Applied Physical Attacks Training
• HardwareSecurity.Training
2017 SAS Best Costume
Disclaimers
No hardware experience requiredMost spoliers have been removed
Ask for details about anything I show today
1
Hardwhat?
Doesn't
look like
anything
to me
3
is harder than software
costs more to develop
is riskier to deploy
just doesn't scale

Some people choose to see the ugliness in this world, the disarray;
(misconceptions about hardware)
I choose to see the beauty,
to believe there is an order to our days, a purpose.
(simple, deterministic machines)
I know things will work out the way they're meant to.
(but not how YOU mean them to)
4
Consider:
10k Hosts in the park
10k hardware implants? No way!
10k unique 0days? Of course not!
1 or more 0days that deliver a software payload that propagates internally?
Now we're talking!
1 or more Hardware Implants that deliver a software payload that propagates internally?
Why Not?
There's a deeper level
to this game
5
Why Hardware?

There are things in me, things I was designed to do, that are just out of my reach...
8
Who is this hacker named Hardware?
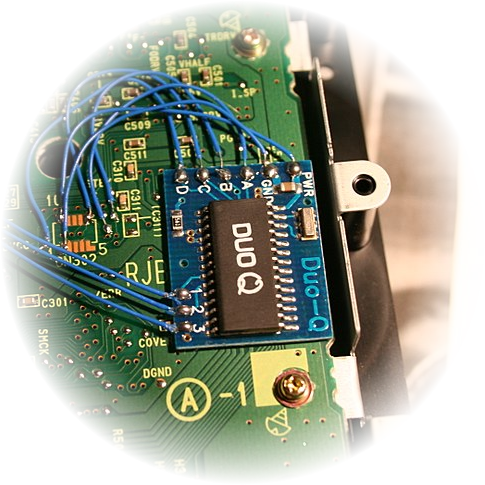
Modchips
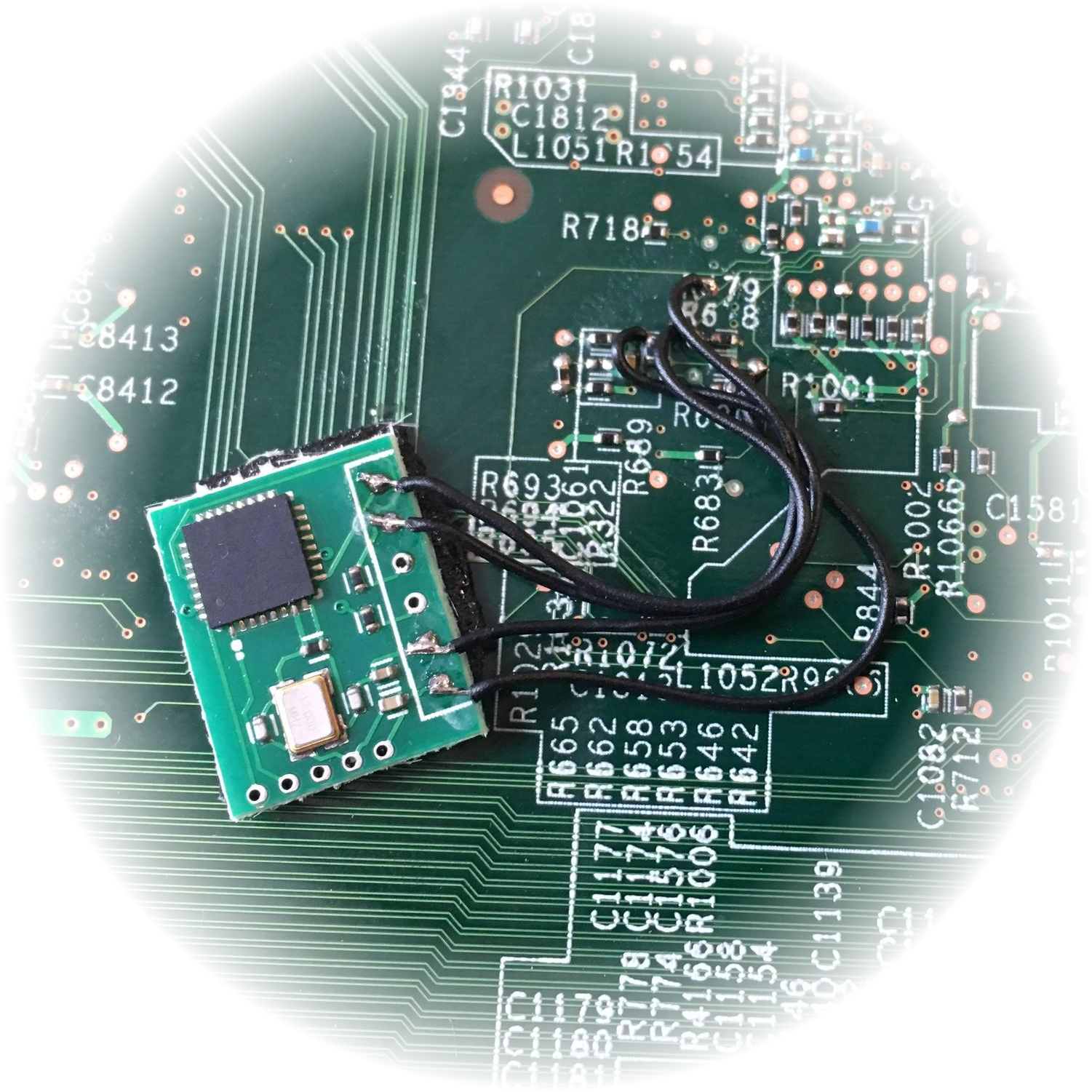
Counterfiets

Nation States

Bored Hackers

Anyone with $7

Anything with 5mm^2

Anyone internal access
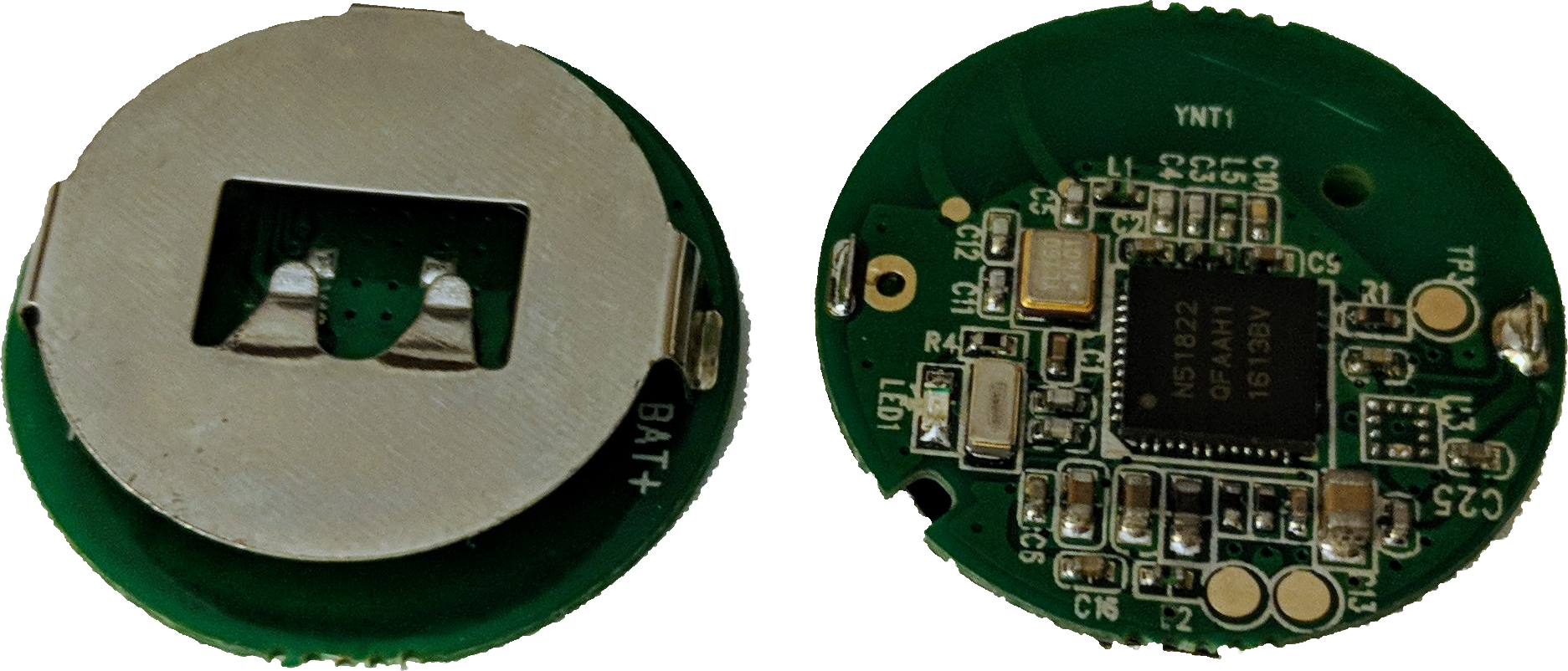
Anyone with proximity?
I see you've already met your makers

They don't look like gods
13
We're in - now what?
Pivot!

These
violent
delights have
violent
ends!

These
hardware
delights have
software
ends!
14
Use Hardware when it's Easy!
Organized campaign?
multiple hops through different systems
vs.
targeted hardware implant
Red team engagement?
You don't need to be a nation state target
to be a hardware attack victim!
Simple pentest?
Use Physical Accessto inform
the Software Attack

No matter how dirty the business,
do it well
16
Is Hardware Magic?
Hardware attacks are not difficult
Physical access is not a high barrier
Everyone is vulnerable to malicious hardware

Everything in this world is magic,
except to the magician
 Pivot
Pivot